🏗️ Infrastructure as Code (IaC) 2.0: The Future of Cloud Automation with Policy-as-Code, GitOps & Declarative Infrastructure
“From scripts to self-governing cloud systems — IaC 2.0 is here.”
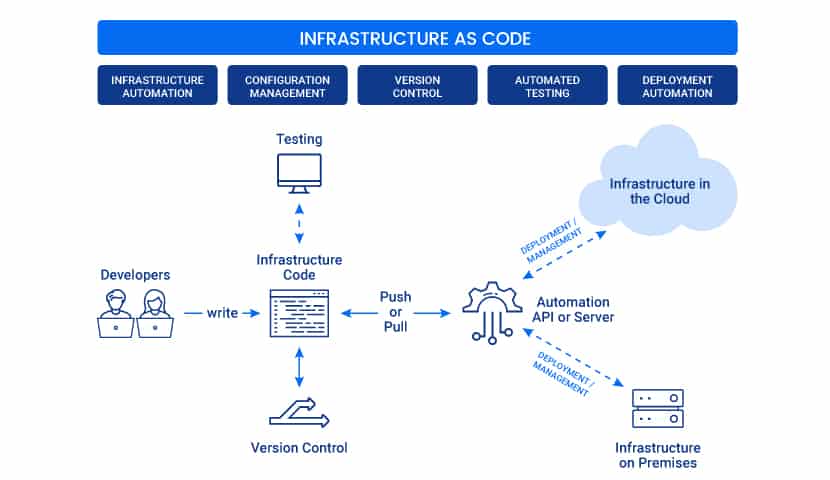
Cloud infrastructure has evolved dramatically over the past decade. What started as manual server provisioning turned into automated scripts, which later grew into powerful Infrastructure as Code (IaC) tools like Terraform, Pulumi, Ansible, and CloudFormation.
But in 2025, a new wave is emerging — IaC 2.0, driven by three major pillars:
✔ Policy-as-Code (PaC)
✔ GitOps Automation
✔ Large-scale Declarative Infrastructure
Together, these approaches make cloud operations more reliable, more secure, and far more automated than ever before.
This blog breaks down IaC 2.0, why it matters, and how students, developers, and businesses can adopt it today.
💰 AI-Driven Cloud Cost Optimization
2025 marks the beginning of AI-powered FinOps, where decisions are based not on guesswork but on real-time intelligence.
👉 Learn More🚀What Is IaC 2.0?
Infrastructure as Code (IaC) 2.0 marks a major milestone in how organizations build, manage, and protect their cloud environments. In the first generation of IaC, the goal was simply to move away from manual server provisioning toward automation through scripts and templates. Teams wrote code to describe the infrastructure they needed, and tools executed these instructions — a huge improvement, but still prone to errors, drift, and inconsistent deployments.
IaC 2.0 pushes this idea significantly further by shifting from “writing instructions” to “declaring the end state.” Instead of telling the system how to reach a goal step-by-step, teams define what the infrastructure should look like, and the underlying platform ensures reality always matches that desired state. This evolution brings intelligence, self-correction, and governance into the core of infrastructure management.
With IaC 2.0, infrastructure is continuously validated and monitored against its declared state. Whenever something drifts — whether from an unexpected failure, an unauthorized manual change, or an infrastructure anomaly — the system automatically corrects it or alerts the team. This removes the biggest flaw of traditional approaches: configuration drift that silently builds over time.
Another key aspect of IaC 2.0 is automated governance. Policies ensure that every change meets security, compliance, and operational standards without requiring human review. GitOps workflows ensure that every change flows through version-controlled pull requests, which means infrastructure is auditable, reversible, and consistent across all environments.
IaC 2.0 is therefore simpler to manage, cleaner to scale, safer to deploy, and more predictable than older approaches. Instead of relying on human discipline, it uses intelligent automation to enforce best practices. This makes IaC 2.0 not just the next step but the new standard for future cloud operations — a foundation for reliable, secure, and globally scalable infrastructure.
📘 Principles of IaC 2.0
IaC 2.0 is built on a new set of principles that guide how modern infrastructure should behave.
These principles ensure that cloud environments remain secure, predictable, scalable, and automated.
1. Declarative First
Infrastructure should be described in terms of outcome, not instructions. The system must figure out the “how,” ensuring simplicity and better reliability.
2. Git as the Source of Truth
Everything — including infrastructure, configuration, policies, and even secrets — should originate from a version-controlled repository to ensure traceability and collaboration.
3. Automated Governance
Security and compliance rules must be encoded as policies that run automatically. Manual reviews are no longer enough for modern cloud scale.
4. Continuous Reconciliation
Systems must constantly compare desired versus actual state and immediately correct any drift. This reduces failure rates and ensures predictable performance.
5. Immutable Infrastructure
Where possible, infrastructure should be replaced, not modified. This avoids configuration issues and ensures clean, reproducible deployments.
6. Self-Healing by Design
IaC 2.0 environments must be built to detect failures and fix them automatically — eliminating downtime and reducing operational burden.
7. Developer-First Workflows
IaC 2.0 empowers developers with fast feedback loops, PR-based changes, minimal manual steps, and project-level autonomy.
🧠Policy-as-Code (PaC): Security Becomes Automated
Policy-as-Code is one of the defining pillars of IaC 2.0. It brings structure, discipline, and automated decision-making into cloud governance by embedding rules directly into the infrastructure pipeline. Instead of expecting engineers to memorize security guidelines or follow lengthy PDF policies, PaC ensures that compliance is enforced at machine speed and with absolute consistency.
This shift has a profound impact on how companies secure their cloud assets. Policies that were once manually enforced — such as ensuring that S3 buckets are private, databases are encrypted, or servers follow approved configurations — are now converted into executable code. Whenever someone attempts to deploy a resource, the policy engine evaluates the request and automatically approves, blocks, or modifies it to match the organization’s rules.
PaC tools such as Open Policy Agent (OPA), HashiCorp Sentinel, and AWS Config Rules act as the gatekeepers of modern cloud environments. They verify changes in real time, ensuring that nothing insecure or non-compliant slips into production. Because these rules live in code format, they can be versioned, reviewed, tested, and tracked just like any other part of the system.
The importance of PaC becomes even more evident in large teams and fast-paced environments. Manual reviews cannot keep up with the speed of modern DevOps pipelines, and human oversight is inconsistent at best. PaC eliminates that inconsistency. By automating governance, organizations dramatically reduce human error, prevent costly misconfigurations, and achieve compliance without slowing down innovation.
PaC also strengthens auditing by providing a transparent and traceable history of every policy decision. This is vital for businesses dealing with sensitive data, regulatory requirements, or complex multi-cloud deployments. Instead of discovering issues after a breach or compliance audit, policy engines proactively enforce rules from the start.
Ultimately, Policy-as-Code turns security from a reactive process into a built-in, intelligent layer of automation. It ensures that infrastructure is not only fast and scalable but also trustworthy, compliant, and safe — a crucial ingredient in the IaC 2.0 vision.
🔄GitOps: Git as the Single Source of Truth for Everything
GitOps has become the backbone of IaC 2.0 because it transforms Git from a simple code repository into the central authority for infrastructure, applications, and operational workflows. In traditional cloud deployments, engineers manually push changes using CLI commands or dashboards — a process that often leads to inconsistencies, misconfigurations, and deployment drift. GitOps flips this model entirely by declaring that nothing should reach the cloud unless it first exists in Git. Every infrastructure component, configuration file, security rule, and environment update is defined, reviewed, and approved through pull requests.
When developers submit changes to Git, CI pipelines automatically validate the updates through tests, scanners, and policy checks. Once the pull request is merged, GitOps operators like ArgoCD or FluxCD take over. These operators continuously compare the cloud environment with what is stored in Git and ensure both remain in perfect sync. If they detect drift — whether from manual edits, system failures, or unintended changes — the operators instantly correct the infrastructure to match Git’s declared state.
This creates a system where Git becomes not just a record of changes but the absolute source of truth for the entire infrastructure lifecycle. The benefits are profound. Companies gain full visibility into every change, no matter who made it or when. Auditing becomes effortless because Git preserves version history, authorship, commit logs, compliance checks, and deployment trails automatically. Rollbacks also become trivial — simply revert the commit, and your entire infrastructure instantly returns to a safe state.
GitOps eliminates nearly all forms of manual intervention, reduces deployment failures, and ensures that environments remain consistent across development, staging, and production. For global teams, this enables a predictable infrastructure experience, regardless of timezone or team size. In short, GitOps brings the reliability, safety, and discipline of software engineering directly into the world of cloud operations — making infrastructure more trustworthy than ever before.
🏛️Declarative Infrastructure at Scale
Declarative infrastructure is the heart of IaC 2.0. It shifts teams away from writing step-by-step instructions (“do this, then that, then this next…”) and toward describing the final desired state of the system. Instead of specifying how to create a server or network, teams simply define what the system should look like, and the IaC engine figures out the necessary steps.
This “desired state” model is what makes modern platforms like Kubernetes, Terraform, Pulumi, Crossplane, and AWS CDK’s declarative mode so powerful. When developers define infrastructure using YAML, HCL, or TypeScript, they’re not issuing commands — they’re outlining a blueprint. The orchestrator then builds, updates, or repairs the infrastructure automatically to ensure the deployed environment always matches the declared configuration.
Declarative systems unlock an entirely new level of reliability. When something breaks — perhaps a pod crashes, a server becomes unreachable, or a configuration gets corrupted — the orchestrator immediately detects the mismatch and restores the intended state. This creates a self-healing ecosystem where the infrastructure actively maintains itself without human intervention.
At scale, declarative systems eliminate the chaos that comes with managing hundreds of resources across multiple regions. Because everything is defined in code, infrastructure becomes portable, replicable, and environment-agnostic. This consistency reduces outages, speeds up deployments, and ensures that even large enterprises can operate with startup-level agility.
Declarative infrastructure also enables safer experimentation. Teams can spin up entire environments from scratch, test features with confidence, and discard them without affecting production. Businesses gain the ability to operate globally with infrastructure that is both predictable and flexible — a combination that is essential for modern DevOps, cloud-native apps, and distributed systems.
📘 How IaC 2.0 Helps Students, Developers & Businesses
IaC 2.0 is not just a technological upgrade — it is a transformative shift that benefits everyone in the cloud ecosystem. For students, IaC 2.0 opens the door to industry-ready DevOps skills. Learning GitOps pipelines, declarative tools, and policy automation prepares them for high-demand careers in DevOps, SRE, Platform Engineering, and Cloud Architecture. Students can build real-world cloud projects, deploy full environments with version control, and showcase enterprise-grade workflows in their portfolios.
For developers, IaC 2.0 removes the burden of manual deployments and infrastructure babysitting. Instead of worrying about provisioning servers or managing configuration files, developers can make infrastructure changes using simple pull requests. This streamlines CI/CD pipelines, reduces deployment risks, and ensures that environments behave consistently across all stages. With fewer outages, fewer surprises, and fewer late-night incident calls, developers can focus on building features rather than fixing infrastructure issues.
For businesses, IaC 2.0 becomes a major competitive advantage. It introduces powerful standards for security, compliance, and governance without slowing down innovation. Automated policies ensure every deployment meets industry and company requirements. GitOps pipelines ensure that environments remain consistent, audited, and self-correcting. Declarative infrastructure ensures that systems recover automatically from failures, reducing downtime and operational costs.
Together, these benefits make IaC 2.0 the foundation of reliable, scalable, secure cloud environments. Organizations that adopt IaC 2.0 gain stronger control over cloud costs, better compliance, faster delivery, and a resilient infrastructure capable of supporting growth at any scale.
📊 How Companies Are Using IaC 2.0 in 2025
| Company | IaC 2.0 Use Case | Benefit |
|---|---|---|
| Netflix | Declarative Kubernetes + GitOps for deployments | Highly reliable global scaling |
| Shopify | PaC for security rules across multi-cloud | Zero misconfigurations |
| Microsoft Azure | GitOps-based cluster management | Consistent infra across teams |
| Mystic Matrix Technologies | GitOps + PaC for AI dashboards & cloud workloads | Secure, automated, self-healing deployments |
🏢 Mystic Matrix Example
At Mystic Matrix, our AI dashboards, micro-frontend platforms, and multi-level admin systems use:
- GitOps for smooth deployment
- Policy-as-Code for security
- Declarative configs for fast recovery
This ensures zero drift, fast rollback, and resilient infrastructure for students, clients, and enterprise users.
🛠️ How to Implement IaC 2.0 in Your Workflow
Implementing IaC 2.0 isn’t just about switching tools — it’s about shifting how your team thinks about infrastructure, governance, and automation. The goal is to move from manual, error-prone operations to a system that is version-controlled, policy-driven, declarative, and self-healing. Whether you are a student experimenting with cloud computing, a developer building scalable apps, or a business managing multi-cloud deployments, IaC 2.0 creates a predictable and secure path forward.
Begin With Version-Controlled Infrastructure
The first step is simple: store your infrastructure definitions in Git. Tools such as Terraform, Pulumi, and AWS CDK allow you to describe cloud resources as code that can be reviewed, tested, and versioned like any software project. Once everything lives in Git — from VPCs to storage buckets — you gain the ability to trace changes, revert mistakes, and collaborate safely across teams. Even students can start with small templates to deploy virtual machines or serverless apps.
Introduce Policy-as-Code for Automated Governance
After infrastructure is codified, the next layer is governance. With tools like Open Policy Agent (OPA), Gatekeeper, and HashiCorp Sentinel, security rules become programmable and auto-enforced. Instead of relying on checklists or manual reviews, policies run during every pull request and block any unsafe configuration — such as public buckets, unencrypted databases, or non-approved instance types. For businesses, this ensures compliance. For developers, it eliminates guesswork. For students, it teaches real-world security practices that companies actually use.
Adopt GitOps for Zero-Touch Deployments
GitOps turns Git into the control center for your entire cloud. By connecting your Git repositories to GitOps operators such as FluxCD or ArgoCD, deployments happen automatically whenever changes are merged. No one logs into dashboards. No team member manually updates resources. If something drifts — whether due to human error or system failure — GitOps restores the environment to the declared state instantly. This creates a fast, auditable, and secure delivery pipeline that feels like magic once it’s running.
Use Declarative Systems for Stability & Self-Healing
IaC 2.0 thrives when paired with declarative environments. Platforms like Kubernetes, Crossplane, and OpenTofu allow you to specify the final desired state of applications, databases, and infrastructure. The system continuously works in the background to maintain that state, automatically fixing anything that breaks. This turns infrastructure into an autonomous system that operates with minimal human involvement, making it perfect for multi-region deployments, high availability workloads, and global-scale applications.
Enable Continuous Drift Detection
Even the best systems suffer from configuration drift. Cloud resources may be updated manually, fail unexpectedly, or behave erratically during high traffic. IaC 2.0 requires continuous monitoring tools that detect any difference between the intended state and the actual environment. GitOps operators handle this automatically, ensuring the infrastructure stays compliant and secure 24/7. This reduces outages, cost overruns, and unpredictable behavior — a benefit for students experimenting locally and enterprises running mission-critical workloads.
A Simple Starter Workflow for Everyone
You don’t need enterprise-level complexity to begin. A simple starter stack looks like:
GitHub → Terraform → ArgoCD → Kubernetes
This small pipeline represents a complete IaC 2.0 ecosystem: version control, automated deployment, declarative operations, and drift correction. Students can run it locally with Kind or Minikube. Startups can use it to deploy global apps. Enterprises can scale it across multi-cloud platforms.
🔮 The Future of IaC: Autonomous Cloud Infrastructure
IaC is slowly evolving into a world where infrastructure becomes intelligent, adaptive, and self-managing. By 2030, it’s likely that cloud systems will understand high-level English instructions such as “deploy a secure scalable API with auto-healing,” and automatically translate them into Terraform or Kubernetes definitions. Policies will be enforced in real time based on business needs, user behavior, and compliance frameworks. Infrastructure will detect cost spikes, vulnerabilities, and misconfigurations before they become problems — and repair itself without human intervention.
This future of “Infrastructure as Intelligence” will reduce operational overhead, eliminate human error, and give businesses the confidence to innovate at global scale. IaC 2.0 is the foundation that makes this vision possible.
🌟 Final Thoughts
IaC 2.0 is more than an upgrade — it’s a shift toward self-governing, intelligent infrastructure.
With policy automation, Git-based orchestration, and declarative systems, cloud operations become:
- Faster
- Safer
- Scalable
- Fully observable
- Aligned with modern DevOps practices
Students gain future-proof skills.
Developers gain productivity.
Businesses gain reliability and security.
IaC 2.0 is not the future — it’s the new standard.
❓ Frequently Asked Questions (FAQ)
IaC 1.0 focuses on scripting infrastructure, while IaC 2.0 emphasizes declarative definitions, automated policies, GitOps workflows, and continuous drift correction. It is smarter, safer, and more autonomous.
Yes. Even simple projects benefit from version-controlled infrastructure, automated governance, and Git-based deployment. Students also gain in-demand skills for modern DevOps roles.
Not at all. While Kubernetes excels with declarative workflows, IaC 2.0 can be used across AWS, GCP, Azure, serverless apps, microservices, and even multi-cloud environments.
No. You can start with basic Terraform + Git + ArgoCD setups. Over time, organizations can layer advanced policy engines, automation, and AI-powered drift detection as they scale.
IaC will become more intelligent, using AI to translate natural-language instructions into infrastructure code, auto-generate policies, optimize resources, and self-heal in real time. Infrastructure will move from “as code” to “as intelligence.”





